Defensive Risk Management

At some point in our driving careers, most of us take a defensive driving course. They’re generally not very complicated – a mix of classroom instruction and behind-the-wheel demonstrations, designed to illustrate some of the hazards of being out on the road and techniques for handling them.
As a business owner, Information Security should be exactly like a defensive driving course. It’s an opportunity to learn about the risks, and an opportunity to learn about the ways you can mitigate those risks.
It goes beyond that, too. When you take that defensive driving course, you don’t just absorb every detail from the instructor and copy it in your daily routine. You evaluate the risk and rewards and adjust accordingly. Some risks you judge as critically important and make changes, while others are less likely and so don’t require as much attention. Those judgements are going to be different for everyone, and they depend on unique aspects of your situation that no one else can adequately judge.
So when we’re talking about information security, how does this work?
Threat Modeling
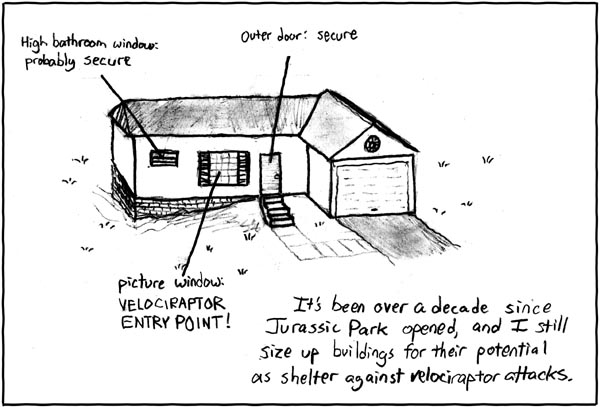
Threat modeling is without question the single most crucial factor in making decisions about your security. The good news is, you already know how to do it – you use threat models every single day of your life.
When you leave your house, do you lock the front door? Whether or not you do depends on your threat model. It’s based on three factors:
- How valuable are the contents of your house?
- Who might be a threat to the things in your house if the door is unlocked?
- What is the likelihood that bad things will occur if the door is left unlocked?
Now, for most things – including locking our front doors – the threat model we use is very simple. The things in my house are extremely valuable and important to me; the front door lock protects against burglars, vandals, and velociraptors; I live in a low crime area and velociraptors have not been spotted in the vicinity recently. So, the risk of one of these negative outcomes occurring is low. Yet the impact, should one of them happen, is very high, and locking my door is both easy and has very little impact on my activities. So I lock the door. You probably go through a very similar process (especially if you saw Jurassic Park at an early age) and you do it so quickly that it doesn’t even register as a conscious action.
The threat model for your business is more complex, but not because of anything to do with the process or the reasoning – it’s just that your business has more complex factors to consider, from your customer data to point of sale devices to inventory and employee information. These factors all have different methods of measuring risk that can be used, but there’s nothing secret about it. It’s asking questions, figuring out the answers that apply to your situation, and then making decisions accordingly.
Risk Management – Not Elimination
Let’s say we’re talking about your business – we’re building your threat model – and we discover there’s a risk you haven’t previously considered. Your first response is likely to be “well, how do I eliminate that risk?”
Here’s the thing – you probably can’t.
Let’s go back to our front door example. We’ve locked our front door – does that mean burglary, vandalism, or velociraptor attacks are now impossible? No, of course not. We’ve reduced the risk, but we haven’t eliminated it. There are other doors, windows, maybe a garage – plenty of other opportunities for someone or something to get in even if the front door is locked. There are other steps we could take to further reduce the risk, but they require more expense and more effort on our part. They might even introduce new risks. Suppose we added a home alarm system on all the doors and windows. Better security, right? Well, we’ve probably reduced the risk some more, especially if it’s obvious there’s an alarm system. But it’s also more work and expense for you and your family. You now have fewer resources to deal with other expenses. You increase the risk of the alarm being triggered accidently and causing you more stress. And at the end of the day, it’s still not impossible for someone to break in or damage your home.
The point is, your threat model and your response to it is all about making decisions and being aware of threats and responses. The choices you make will better prepare your business, even in the cases where you don’t decide to change anything, because they will at least be conscious choices to accept certain risks rather than simple inertia.
Offload Execution, Not Control
The implicit promise of most modern security software is “eliminate the security problems”. Buy this product and stop malware. Buy that product and eliminate phishing attacks. Buy, buy, buy, and you’ll not only be perfectly secure, it might even make perfect French fries in your microwave.
Well, as we just discussed, you can’t actually eliminate the risks And even if you could, doing so wouldn’t free you from the responsibility for making the decisions. What you really need isn’t a better tool or a more expensive service provider, it’s a partner who can work with you to identify the risks and help you manage them effectively. Give you the tools and the techniques to make the decisions, and then go execute on those decisions for you while you get back to managing your business.
In the sailing world, a captain can hire a crew to do all the jobs they don’t have the ability, desire, or capacity to handle on their own. But they’re still the captain, still in charge, and still making the decisions.
Let us crew your boat for you.